Linux Privilege Escalation Using LD_PRELOAD
LD_PRELOAD is an environment variable in Linux that allows users to load custom shared libraries before any other libraries during the execution of a program. Attackers can exploit this feature to inject malicious code and potentially escalate privileges, especially if the target program is executed with elevated permissions (e.g., as root).
How LD_PRELOAD Works
- Purpose: LD_PRELOAD is used for debugging or testing by overriding functions in shared libraries.
- Mechanism: When a program is executed, the dynamic linker checks the LD_PRELOAD variable for a shared library path. If specified, this library is loaded before others, allowing its functions to override standard library functions.
Privilege Escalation

Let’s generate a C program file inside the /tmp directory.
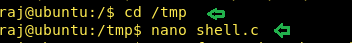
| |
Save it as shell.c inside /tmp.

Next, compile it to generate a shared object with a .so extension, similar to a .dll file in the Windows operating system. Enter the following command:
| |
Check the generated file:
| |
Now execute the find command with LD_PRELOAD set to the path of the shared object:
| |
To verify the privileges, run:
| |

And finally, you should have obtained root privileges! 😉
